Since the release of PoshC2 we’ve been hard at work to improve the tool and we’ve recently added some more payloads to the tool.
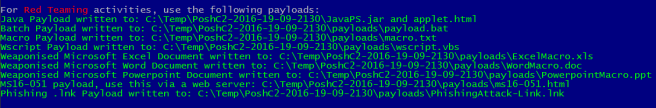

In addition to the original payloads we’ve added new weaponised Excel, Word and PowerPoint documents. These are blank documents that have the implant embedded into them, ready for you to add content to.
We’ve added a payload that exploits the MS16-051 Internet Explorer – vbscript_godmode vulnerability. Credit goes to – http://theori.io/research/cve-2016-0189 for the exploit. The html payload can be copied directly to a webserver were victims can be directed to in a Red Team or social Engineering attack.
As can be seen above there is a revised layout to the engagement folders, a much cleaner layout.
Further work to improve the whole tool are ongoing and further new features are planned.
Get PoshC2 here – https://github.com/nettitude/PoshC2, also checkout the wiki for detailed information on features and usage po PoshC2.