Following on from the previous post, I’ve improved the MS08_067 scanner by removing the sledge-hammer approach, ie scan everything, to a more defined and controlled approach, ie get some hosts, work out if they might be a windows box and then scan.
Here is the script;
<ruby>
###########################################################
#Must set Global RHOSTS via setg RHOSTS xxx.xxx.xxx.xxx/xx#
###########################################################
#Check to see if RHOSTS is set Globally
if (framework.datastore['RHOSTS'] == nil)
print_line("Please set RHOSTS globally with this command setg RHOSTS xxx.xxx.xxx.xxx/xx...exiting")
return
end
#Populate the datastore with some Hosts
#######################################
#Setup NMAP Options
nmapopts = "-O -T 5"
run_single("db_nmap #{nmapopts} #{framework.datastore['RHOSTS']}")
#Remove RHOSTS
run_single("unsetg RHOSTS")
framework.db.workspace.hosts.each do |host|
host.services.each do |serv|
next if not serv.host
next if (serv.state != ServiceState::Open)
if (serv.name =~ /smb/ or serv.name =~ /microsoft-ds/ or serv.name =~ /netbios/ or serv.port == 445 or serv.port == 139 or serv.port == 137)
if(serv.port == 445)
run_single("use exploit/windows/smb/ms08_067_netapi")
run_single("set RHOST #{host.address}")
run_single("check")
end
end
end
end
</ruby>
Some changes to the way the resource script works, first we need to set the Global variable RHOSTS, this can be set via the ‘setg RHOSTS xxx.xxx.xxx.xxx/xx’ command.

Then we just fire up the resource script as before, but this time you will get a bunch of nmap output.
I used a db_nmap scan to populate the database

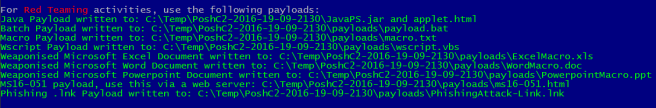
Then, if there are any Windows hosts on the network with the correct services listening, you will see this;

And the rest is down to you…Enjoy
Credit to the MSF guys, as a couple of lines of code were taken from the default resource scripts that ship with the framework and of course to @mubix for the initial rapid psexec script that this was based upon.